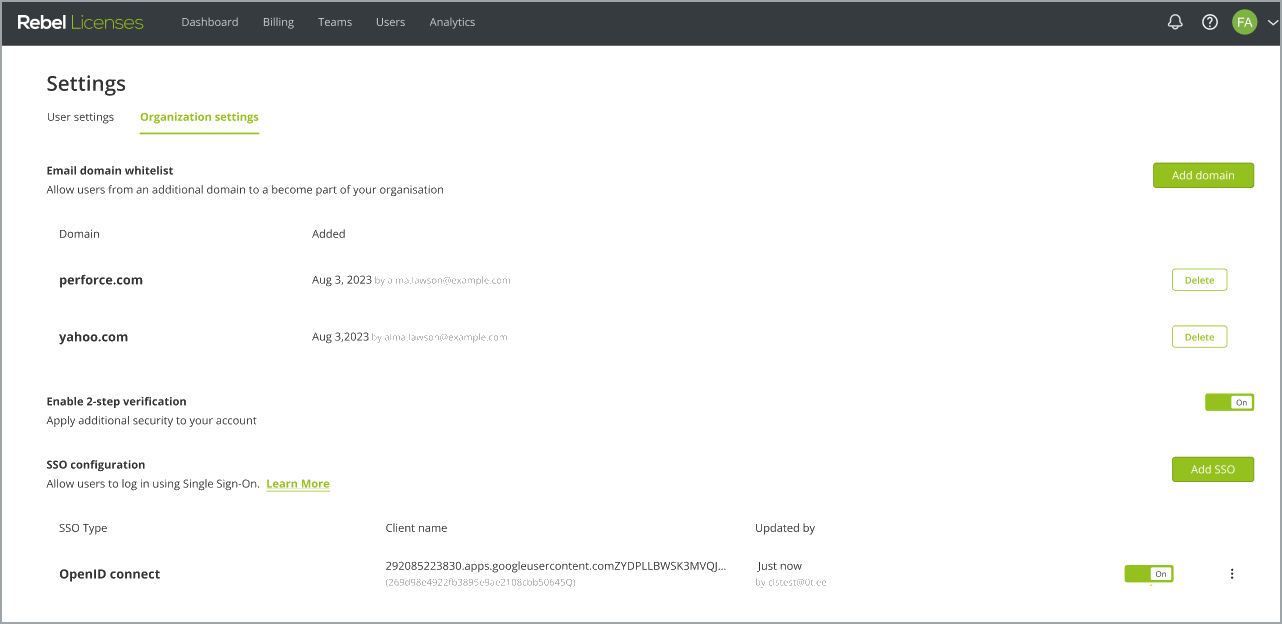
Organization settings¶
The Organization settings enable you to configure single sign-on to authenticate users by using the OpenID Connect (OIDC) authentication method. You can use OpenID Connect to configure single sign-on between a Cloud License Server and a third-party identity provider. For more information, see OpenID Connect.
Note
You can add multiple SSO configurations, but only one configuration can be enabled.
To configure SSO, you must have an Organization Admin or Organization Owner role.
Prerequisites for OpenID Connect¶
Before you begin
Verify that the Identity Provider (IdP) supports the OpenID Connect Discovery Endpoint and uses the standard Well-Known Configuration metadata values. For more information, see OpenID Provider Metadata.
Set the Client Authentication method to use HTTP POST to authenticate with the Authorization Server, as CLS only supports this method. If your identity provider defaults to basic HTTP authentication, consider using HTTP POST. For more information, see Client Authentication.
Verify that the Scopes include the openid and email scope values. The CLS will request the openid and email scopes from the identity provider by using the OpenID Connect scope parameter. While the openid scope is mandatory and enabled by default, some identity providers may require the email scope to be explicitly added and enabled.
Configure OpenID Connect SSO¶
You can use OpenID Connect for single sign-on authentication with CLS. To set up single sign-on authentication by using OpenID Connect, you need to create an OpenID Connect client application with your identity provider. Refer to the documentation of your OpenID provider to obtain the Client name, Client ID, Client secret, CallBack URL, and Discovery URL configuration values.
After you have created the client application with your identity provider, you can configure SSO in CLS.
To add an SSO configuration
Go to the Settings > Organization settings > SSO configuration > Add SSO. The Add OpenID Connect SSO dialog box opens.
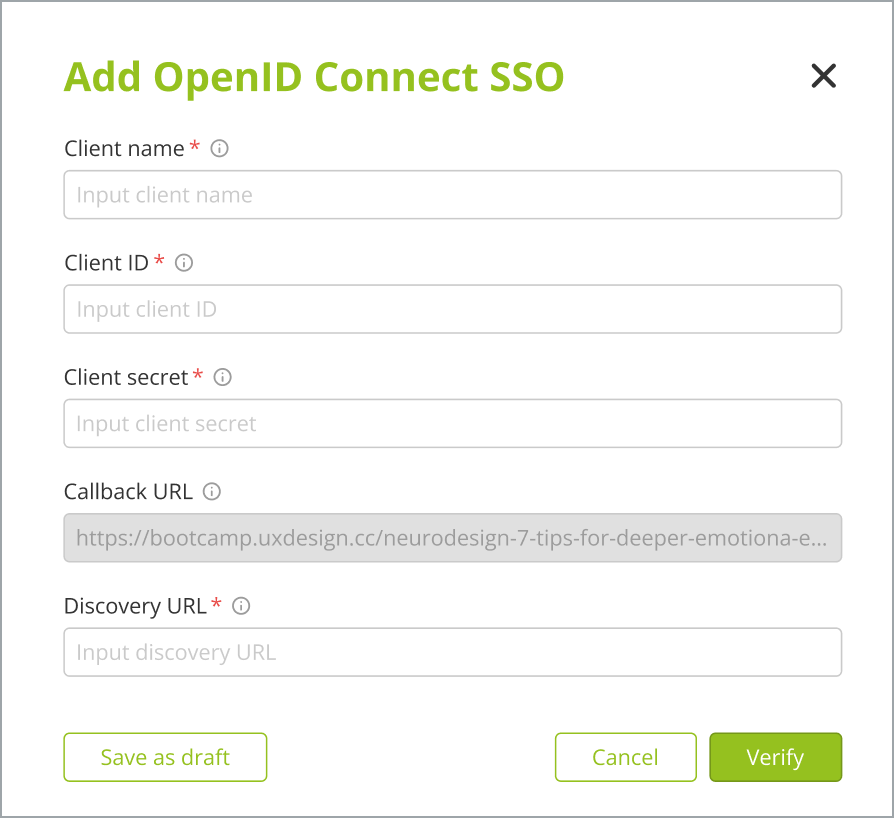
In the Add OpenID Connect SSO dialog box, type the SSO details as shown in the following table.
Field
Description
Client name
The unique name for the OIDC client application.
Client ID
The unique identifier of the application created upon registration with the identity provider.
Client secret
The client secret of the application created upon registration with the identity provider.
CallBack URL
The callback URL registered with the identity provider. The callback URL is where the identity provider sends the authentication response for the CLS application.
Discovery URL
The discovery URL of the identity provider you want to connect to is the well-known configuration URL with a structure /.well-known/openid-configuration.
Click Verify.
Verify the SSO¶
After adding an SSO configuration, you must verify it. The verification can be done when the SSO configuration is saved as a draft or when the verification is pending.
To verify the SSO
Follow these instructions to verify the SSO when the configuration is saved as a draft.
Go to the Organization settings > SSO configuration and click Edit SSO. The Edit SSO dialog box opens.
Check the relevant fields and then click Verify.
To verify the SSO after the configuration is added, even if the verification is pending.
Go to the Organization settings > SSO configuration and click Verify Now.
You are redirected to the identity provider page to complete the verification.
Enable and Disable the SSO¶
After you have verified the SSO, you can enable it.
To enable the SSO
Go to the Organization settings > SSO configuration and turn on the toggle under SSO Type to enable SSO. The Enable SSO dialog box opens.
Click Confirm.
The SSO is enabled and the users can log in using the single sign-on.
To disable the SSO
Go to the Organization settings > SSO configuration and turn off the toggle under SSO Type to disable the SSO. The Disable SSO dialog box opens.
Click Confirm.
The SSO is disabled and the users cannot log in using the single sign-on.
Sign in with SSO¶
To sign in with SSO, go to the Sign-in to your account page, and click Single sign-on. You are redirected to the identity provider to complete the sign-in process.
Note
If you do not have SSO configured, you can log in to your account by using an email address and password.
Edit, Delete, and View SSO details¶
You can view and edit the configuration of your existing SSO or delete an SSO configuration if you don’t need it.
To edit an SSO configuration
Go to the Organization settings > SSO configuration and click the
 to edit the SSO configuration.
to edit the SSO configuration.The Edit SSO dialog box opens. Edit the relevant fields such as the Client name, Client ID, CallBack URL, Discovery URL, and Client secret.
Click Verify to verify the SSO connection.
To delete an SSO configuration
Go to the Organization settings > SSO configuration and click
 to delete the SSO configuration. The Delete SSO dialog box opens.
to delete the SSO configuration. The Delete SSO dialog box opens.Click Confirm to remove the single sign-on login.
After removing the SSO configuration, the user will need to log in by using an email address and password.
To view the SSO details
Go to the Organization settings > SSO configuration and click ![]() to view the SSO details. The SSO Details dialog box opens to display the SSO details of your existing SSO configuration.
to view the SSO details. The SSO Details dialog box opens to display the SSO details of your existing SSO configuration.
Enable two-step verification¶
To enable two-step verification, turn on the Enable 2-step verification toggle to apply additional security to your account. After enabling two-step verification, every login attempt must be verified by clicking the login link sent to the user’s associated email address. To disable two-step verification, turn off the Enable 2-step verification toggle.
